Appearance
Identifying Spear Phishing Attacks
Beware of "spear phishing" attacks, where bad actors gather information from sources like LinkedIn and company websites, then impersonate management and target specific staff with social engineering tactics, usually via email.
It is rare that the attacker has access to the the actual email account, so most of these attacks can be revealed simply by looking for indications of email forgery.
95% of the time you can identify scam / spam emails just through inspection of the email address and URLs in the message.
Here are a few tips to help you spot them. These apply to general phishing attacks and email scams as well.
The Basics: Top Giveaways
1. Forged Display Name
Did you know?
The Display Name and the email address are separate, and either can be forged.
Look at the actual email address, not just the display name (this is an actual example):
From: Dean Goodman
<mm2.ww3@mail.ru><-- not LGA!
If the email address is concealed, dig deeper. In Outlook for example, hover over the display name and view the popup card:
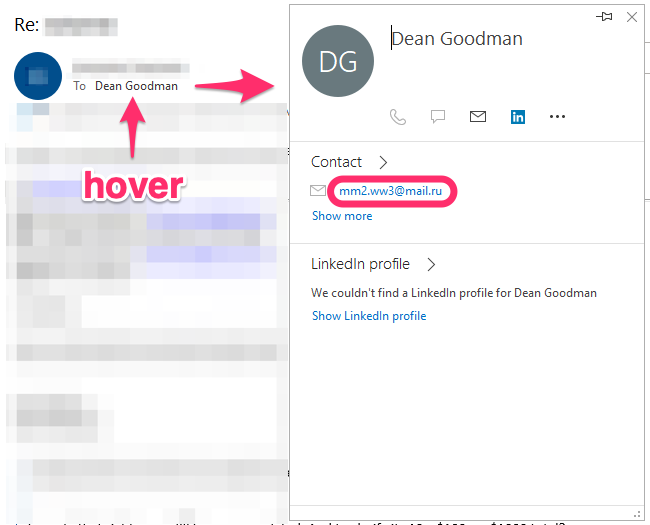
2. Legit From but forged Reply-To address
Did you know?
The From address and the Reply-To address are not the same!
Replies don't always go to the address in the From field. This one can be a little harder to spot because you might not notice until you draft a reply.
From: Dean Goodman
<dean@lga-ap.com>
Reply-To: Dean Goodman<mm2.ww3@mail.ru>
If you only look at the From address you might think this is legit, but when you reply to this message, the To field will be addressed to the scammer.
3. Deceptive Links
Did you know?
Just like email addresses, a URL's target can be different than what's displayed.
Fake display names
Which of these is the real link?
Fake domains
Beware also of more sophisticated attacks that use similar looking letters in URLs. This is easy to spot:
But this is harder:
If in doubt, manually type what you know to be the correct URL into the browser.
4. Requests for money
- "I need you to go buy some gift cards" We've seen this more than once
- "I need you to pay this invoice right away"
- Anything to do with Bitcoin / cryptocurrency
5. Requests for your credentials
Never enter your username, password, or other info into a form after clicking on a link in an email unless you are sure the link is legit.
Other clues
- Bad speling or use wrong grammar
- Urgency: "Do this right now or you'll lose access to your account!" No I won't.
- "I can't talk on the phone but I need you to do this right away!"
- "We detected a recent charge on your Amazon account!" No you didn't.
- "I broke into your computer and have been watching you!..." Nope.
The Future: Artifical Intelligence
Many scams rely on the very simple deception tactics mentioned above. More sophisticated attacks than these already exist, and with the recent explosive growth of AI, techniques using deepfake audio, chatbots, and even deepfake realtime video calls are sure to have a bright future in social engineering!
